
The ever-changing nature of attack and protection technologies makes it necessary to evaluate regularly the protection level of internet exposed infrastructure against the DDoS (Distributed Denial of Service) threat. These evaluations differ from “standard” penetration tests in the essence of the assessed threat that can undermine the availability of systems.
6cure DDoS Assessment®, our unique DDoS testing platform, allows you to evaluate your defense strategy, your processes, your solutions providers and your security provider against DDoS threat by launching safe and fully controlled attacks. Supplement your regular risks analyses by validating the availability SLA of your critical services.
Why perform DDoS resilience test ?
Against the threats represented by DDoS attacks, many organizations equip themselves with on-premise or cloud mitigation solutions whose efficiency must systematically be assessed, with the following challenges:
-
- regularly evaluate protections performance and infrastructures resilience against the continuous evolution of the sophistication, kinetic and frequency of the current and future DDoS attacks;
- check the existing DDoS mitigation solutions adaptation with respect to the evolutions of the organization services architecture, in the context of digital transformation, functions migration to cloud architectures or the rise of remote working solutions;
- identify and eliminate blind spot of protection devices, and evaluate organization and processes of teams assigned to attacks surveillance and response;
- reconsider service-level agreements (SLA) of third parties involved in DDoS attacks response and optimize average costs of the actual mitigation means;
- obtain a global risks assessment and prove the organization’s capacities to manage DDoS threat.
With more than 15 years’ expertise in DDoS, 6cure offers to evaluate the efficiency of your DDoS mitigation strategy by conducting attacks simulation within a fully controlled environment.
Reproducing the botnet models used by real-life attackers, the DDoS Assessment® service makes use of this architecture allows to perform attacks from different cloud geographies.
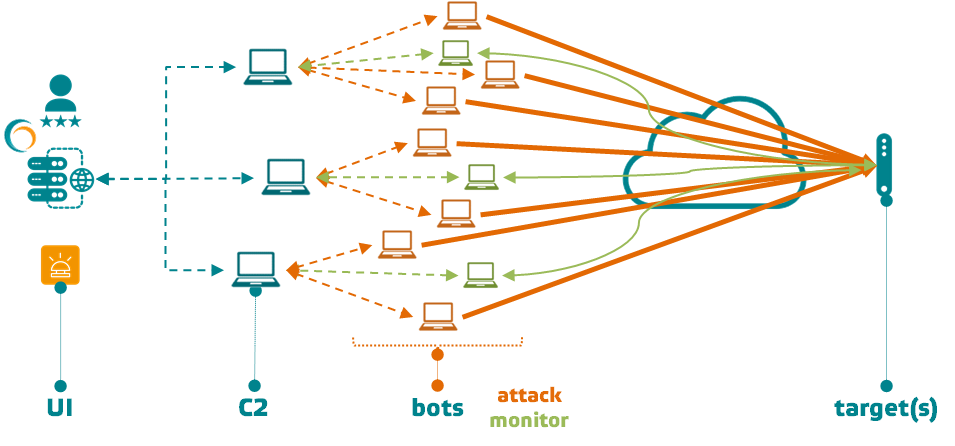
Relying on more than 40 different vectors, these attacks can be divided into 3 categories:
-
- Volumetric attacks: with the ability to generate several tens Gbps of traffic originating from 5 geographic areas, this type of attacks allows to test your capacity to handle a rate, a number of packets and connections that represent a significant load and duration;
- Application attacks: aiming to overload a web server, the generated application requests (e.g., HTTPS) asses the resilience of your mitigation solution against resources exhaustion;
- Logic attacks: difficult to detect and exploiting methods requiring little resources, this type of scenarios aims to check the vulnerability of your infrastructures against protocol breaches.
Available attacks sample
|
|
|
|
|
Controlled evaluation & shared expertise
During the audit, 6cure platform guarantees:
-
- reliability:
- the emergency stop system let you end in less than 5 seconds an ongoing attack anytime
- homogeneous traffic generation is ensured by the platform
- attacks are supervised in real-time thanks to a web interface
- flexibility: traffic provenance can be selected by cloud provider, IP address space and geographical area
- agility: attacks features are re-configurable dynamically during a campaign (vectors, kinetic, geography)
- reliability:
At the end of the campaign, a complete audit report is produced by our experts, it is accompanied by analyses and recommendations to strengthen your protection strategy.
Packages
| Core | Premium | Business | Custom | |
|---|---|---|---|---|
| Assess surface | ||||
| Target services | 1 | 2 | Multiple | Multiple |
| Attacks | 5 | 10 | 20 | Custom |
| Custom attacks | No | No | No | Yes |
| Maximal volume | 2 Gbps | 6 Gbps | 15 Gbps | 20+ Gbps |
| Maximal connections | 10 K | 50 K | 100 K | 100+ K |
| Maximal rate | 500 Kpps | 1 Mpps | 2 Mpps | 5+ Mpps |
| Audit duration | 4h | 8h | 12h | Custom |
| Assess management | ||||
| Audit planning | ✔ | ✔ | ✔ | ✔ |
| Reconnaissance | ✔ | ✔ | ||
| Real-time monitoring and assistance | ✔ | ✔ | ✔ | ✔ |
| Emergency stop | ✔ | ✔ | ✔ | ✔ |
| Non-working hours | ✔ | ✔ | ||
| Audit summary report | ✔ | ✔ | ✔ | ✔ |
| Audit analysis | ✔ | ✔ | ✔ | |
| Expert recommendations | ✔ | ✔ | ||